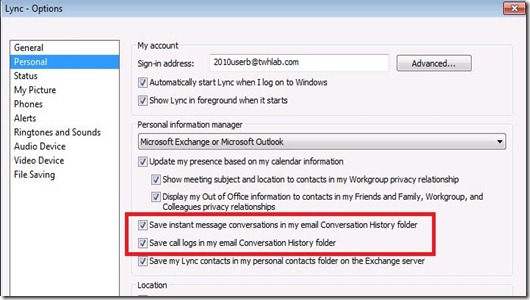
I know that everyone runs the Lync Best Practices Analyzer (BPA) on a regular basis…right? After running the BPA, you might see the following warning:
Pool fully qualified domain name (FQDN) “fqdn” is not found as a http service principal name (SPN) on any user or computer. Kerberos web authentication is not configured..

The warning pops up due to the fact that Lync uses NetworkService to run the Web Services and NetworkService cannot have SPNs assigned to it (this is a change from how OCS handled it).
I am not going to address the “why use kerberos authentication?” because there is already a great article written by Jens Trier Rasmussen. I suggest reading it before proceeding.
The rest of this post will describe the process of enabling Kerberos authentication for the Lync Web Services.
1) Create a Kerberos account
Pre-req: member of Domain Admins and computer running Lync Management Shell (LMS)
From the LMS, run: New-CsKerberosAccount –UserAccount “Domain\UserAccount” –ContainerDN “CN=Users,DC=DomainName,DC=DomainExtenstion”
My command: New-CsKerberosAccount –UserAccount “Homelab\LyncKerbAcct” –ContainerDN “OU=UC Objects,DC=homelab,DC=local”

Note that the –UserAccount parameter is used even though we are creating a computer account with this command.

2) Assign the Kerberos account to a site
Pre-req: member of RTCUniversalServerAdmins and computer running Lync Management Shell (LMS)
To use the Kerberos account, you must assign it to a site. While you can create multiple Kerberos accounts for your environment, you can only assign one account per Lync site.
From the LMS run: New-CsKerberosAccountAssignment –UserAccount “Domain\UserAccount” –Identity “site:SiteName”
My command: New-CsKerberosAccountAssignment –UserAccount “Homelab\LyncKerbAcct” –Identity “site:Datacenter”
Then run Enable-CsTopology

3) Set Kerberos account password and Synchronize to IIS
Pre-req: member of RTCUniversalServerAdmins and computer running Lync Management Shell (LMS)
From the LMS run: Set-CsKerberosAccountPassword –UserAccount “Domain\UserAccount”
My command: Set-CsKerberosAccountPassword –UserAccount “Homelab\LyncKerbAcct”

If any servers are added to the topology in the site (like Front-ends and Directors) you will need to synchronize the Kerberos account password to IIS of the new server.
From LMS run: Set-CsKerberosAccountPassword –FromComputer SourceComputer –ToComputer DestinationComputer
My command: Set-CsKerberosAccountPassword –FromComputer lablyncfe01.homelab.local –ToComputer lablyncfe02.homelab.local

4) Testing to make sure Kerberos is working properly
To test for full functional readiness of Kerberos within a site, the following command can be run to create a report:
From LMS run: Test-CsKerberosAccountAssignment –Identity “site:SiteName” –Report “C:\reportpath\reportname.htm” –Verbose
My command: Test-CsKerberosAccountAssignment –Identity “site:Datacenter” –Report “C:\Temp\KerbTest.htm”
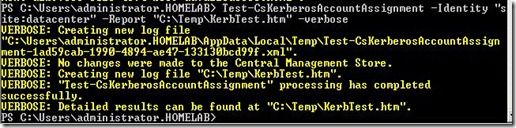
Report generated:

Hope this helps!